Security and AI Governance at Maven AGI: Built In, Not Bolted On
Why enterprise AI adoption requires security architecture, not add-ons
Here’s a conversation that happens more often than most people realize.
A customer is working with a support agent to resolve an issue. During the exchange, they share common account details like their name, email address, phone number, or a customer ID. Occasionally, customers also overshare: a Social Security number, credit card details, or medical information like a diagnosis or prescription name.
The question is simple but critical: what should happen to that data next?
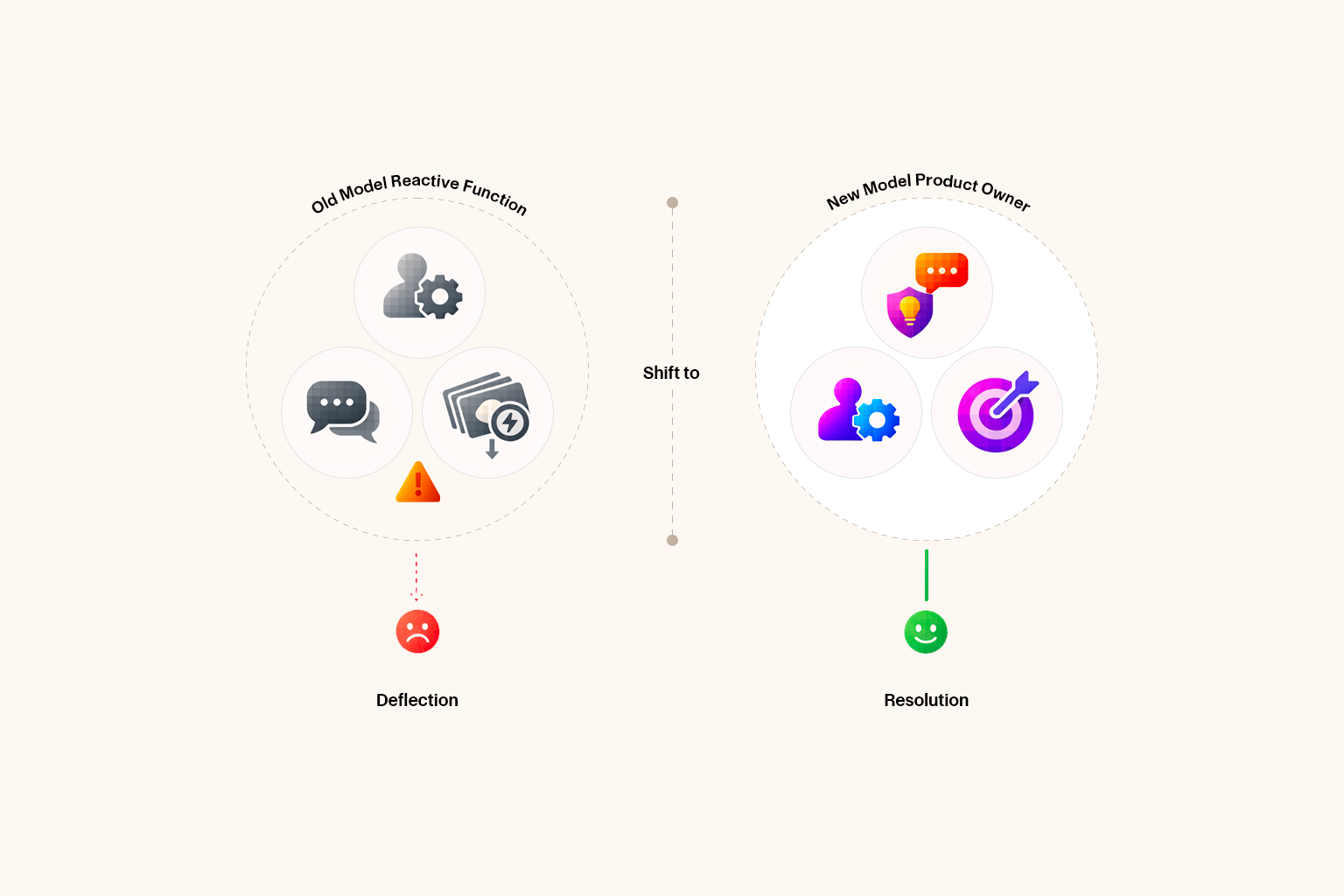
At Maven AGI, we make a clear distinction between approved information and unnecessary sensitive information. Only data explicitly approved for a given use case is allowed to enter the AI processing pipeline. Any unnecessary sensitive data is automatically detected and redacted at ingestion, before it can be used for AI inference, sent to external model providers, written to audit logs, or displayed in agent interfaces.
These controls are policy-driven and consistent. They are not adjusted on a per-conversation basis. Customers define what information is approved for their workflows, and Maven AGI enforces those policies consistently across the platform.
This isn’t a feature added after the fact. It’s how the system was architected from day one.
The Enterprise AI Trust Problem
Enterprise AI adoption is no longer limited by model capability - it’s limited by trust.
Organizations evaluating conversational AI platforms are asking the same practical questions:
- Can this system safely handle sensitive customer data?
- How does it prevent unnecessary exposure of high-risk information?
- How do we demonstrate control effectiveness to auditors, regulators, and customers?
- Can AI be deployed in regulated environments without introducing new risk?
These aren’t theoretical concerns. When a security-forward enterprise customer reviewed Maven’s compliance posture, their immediate response was:
“Our board will be very pleased with this.”
That reaction went beyond features. It was confidence that deploying AI wouldn’t create a governance or compliance liability.
Security as Architecture, Not an Add-On
Maven’s approach is grounded in a simple principle: delegated security.
We don’t ask customers to adopt a new identity or access model. Instead, we integrate with the systems they already trust. Customers define access policies, and Maven AGI enforces them consistently.
This matters because security requirements aren’t uniform. Different industries and organizations operate under different regulatory, operational, and risk constraints. One-size-fits-all security doesn’t work.
At a high level, Maven AGI provides enterprise identity integration, role-based access control, strong authentication for privileged users, comprehensive audit logging, encryption in transit and at rest, tenant isolation, and ongoing independent security testing.
Product Security: The AI-Specific Layer
Traditional security controls are necessary, but they’re not sufficient. AI systems introduce new failure modes that require additional safeguards.
Approved data in. Unnecessary sensitive data out.
Maven AGI uses a customer-defined, policy-enforced allow-list model. Approved data elements, like names, email addresses, phone numbers, and account identifiers, are permitted when required for support workflows. High-risk sensitive data that is not necessary, like Social Security numbers, financial account information, or medical details (for example, diagnoses, treatment history, or prescription names), is detected and redacted at ingestion.
Redaction occurs before external model calls, long-term storage, audit logging, or display in agent interfaces.
Customer data is not used to train models
Maven AGI does not use customer data to train or fine-tune foundational models. Customer data is not aggregated or reused for model improvement.
Safety and adversarial resilience
The platform is designed to identify harmful content and defend against AI-specific threats, including prompt injection, obfuscation attempts, and tactics intended to extract sensitive data or override system behavior.
Grounded answers with traceability
Responses are grounded in customer-approved knowledge sources. Users can see what information informed each response, reducing unsupported outputs and improving auditability.
Human oversight by design
When automation isn’t appropriate, Maven AGI supports escalation to human agents based on configurable signals such as confidence thresholds, customer requests, or conversation risk indicators. Agents receive full context so customers don’t have to repeat themselves.
Validation Through Independent Audits
Strong controls matter. Independent validation reinforces trust.
Maven’s security, privacy, and AI governance practices are verified through third-party audits and certifications, including:
Security & Infrastructure
- ISO/IEC 27001:2022 — Information security management
- SOC 2 Type II — Security, availability, and confidentiality controls
- ISO/IEC 27017 — Cloud security controls
- ISO/IEC 27018 — Protection of personal data in cloud environments
Industry-Specific
- PCI-DSS v4.0 Level 1 AOC — Payment card industry security standards
- HIPAA/HITECH — Healthcare data protection (with BAA available for covered entities)
Privacy
- ISO/IEC 27701 — Privacy information management system
- Data protection processes including DPIAs and records of processing
- Standard Contractual Clauses for cross-border transfers
AI Governance
- ISO/IEC 42001 — AI management system
ISO/IEC 42001 provides independent validation that Maven’s AI systems are governed through defined policies, monitoring, and incident management, not simply deployed and left unchecked.
Security and Governance in Regulated Enterprise Environments
Certifications are important, but they’re part of a broader system.
The real measure of success is whether organizations can deploy AI with confidence: knowing their data is protected, their obligations are met, and their AI systems behave predictably and responsibly in production.
If you’re evaluating conversational AI for enterprise or regulated industries, here are the questions worth asking vendors:
- What information is explicitly allowed into the AI system?
- Where and when is unnecessary sensitive data redacted?
- Is customer data used to train models?
- Which certifications have actually been achieved?
- Can the system be deployed on-premises if required?
- How are prompt injection and other AI-specific attacks handled?
- What happens when AI escalates to a human? Does the customer have to start over?
At Maven AGI, security and AI governance aren’t afterthoughts or marketing claims. They’re the architectural foundation that makes enterprise AI adoption possible.
If you’d like to see this approach in practice, you can request a demo, or visit our Trust Center.
Don’t be Shy.
Make the first move.
Request a free
personalized demo.